Many people have asked me to recommend a good flash drive that they can use for a live, bootable version of BackTrack. While there are many different drives out there, the one drive that caters to the needs of the BackTrack user is the 4GB BackTrack USB Drive from ZBrown Technology Electronics. This drive is only available to users through this blog and is complete with the latest copy of BackTrack ready to boot! More details about the drive can be found on the site by following the link below.
The drive is only $19.99 USD (Includes BackTrack 5) and ships to anywhere in the United States! If anyone outside the US would like to purchase one, please send me an email (i7hacking@hotmail.com) and I will reply with a forgien registration link, which will allow you to register and order on the site.
To order this drive: click here!
To visit ZBrown Technology Electronics: click here!
My goal with this blog is to share the knowledge I have gained over the years about breaking though the limitations of computer security and exposing the loopholes.
Saturday, July 30, 2011
Saturday, July 23, 2011
Easy SQL Injection [Using Havij 1.5]
Introduction:
I received a request from Don Sam to post a tutorial that guided that focused on SQL Injection. SQL Injection itself can be a pretty advanced and overwhelming topic, so I decided to introduce a small, lightweight utility known as Havij. In this tutorial, I'll be using version 1.5.
I will assume you have downloaded Havij and have selected a target website. If you haven't downloaded Havij, you can do so here. If you don't have a target site in mind, you can head on over to the Devil's Blog On Security for a list of common SQL Dorks. All you have to do is choose one, then Google it. The websites in the results are possibly vulnerable! Just copy the web address to the clipboard for use later.
Step 1:
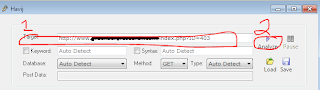
The first thing you need to do is paste the address of your target into the text box labeled Target, then choose Analyze. Havij will then test the target to see if it is vulnerable to SQL Injection.
If the target is vulnerable, Havij will return the name of the database being used at the URI you supplied.
Step 2:
After you have determined that the target is vulnerable to SQL Injection, you need to get a list of all of the tables in the DB. Do this by choosing the Get Tables option.
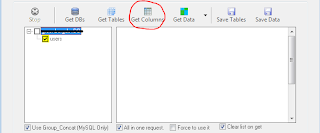
Havij will then return a list of all of the tables in that DB. Check the tables that contain the data you want, then choose Get Columns. This will return a list of the columns in that table.
Step 3:
Once Havij has finished looking for the columns in the table, it will return a list in the tree structure under that table. Check the columns you want, then choose Get Data.
Finally:
As Havij extracts the information from the columns of the table, it will be displayed in the whitespace to the right. Most of the time, this information isn't even encrypted. If it is a column of password, it may be encrypted with an MD5 Hash, but that is pretty easily decrypted!
Conclusion:
So, you have just conducted a successful SQL Injection attack on a vulnerable website. While vulnerable databases aren't as common anymore, there are still many, many, many out there. In my research, I Googled a SQL dork and the first site was vulnerable!
If you have any questions, comments or concerns, please feel free to comment below!
I received a request from Don Sam to post a tutorial that guided that focused on SQL Injection. SQL Injection itself can be a pretty advanced and overwhelming topic, so I decided to introduce a small, lightweight utility known as Havij. In this tutorial, I'll be using version 1.5.
I will assume you have downloaded Havij and have selected a target website. If you haven't downloaded Havij, you can do so here. If you don't have a target site in mind, you can head on over to the Devil's Blog On Security for a list of common SQL Dorks. All you have to do is choose one, then Google it. The websites in the results are possibly vulnerable! Just copy the web address to the clipboard for use later.
Step 1:
The first thing you need to do is paste the address of your target into the text box labeled Target, then choose Analyze. Havij will then test the target to see if it is vulnerable to SQL Injection.
If the target is vulnerable, Havij will return the name of the database being used at the URI you supplied.
Step 2:
After you have determined that the target is vulnerable to SQL Injection, you need to get a list of all of the tables in the DB. Do this by choosing the Get Tables option.
Havij will then return a list of all of the tables in that DB. Check the tables that contain the data you want, then choose Get Columns. This will return a list of the columns in that table.
Step 3:
Once Havij has finished looking for the columns in the table, it will return a list in the tree structure under that table. Check the columns you want, then choose Get Data.
Finally:
As Havij extracts the information from the columns of the table, it will be displayed in the whitespace to the right. Most of the time, this information isn't even encrypted. If it is a column of password, it may be encrypted with an MD5 Hash, but that is pretty easily decrypted!
Conclusion:
So, you have just conducted a successful SQL Injection attack on a vulnerable website. While vulnerable databases aren't as common anymore, there are still many, many, many out there. In my research, I Googled a SQL dork and the first site was vulnerable!
If you have any questions, comments or concerns, please feel free to comment below!
Did you know that i7's Guide to hacking can be delivered daily to your kindle devices? Subscribe Now!
Thursday, July 21, 2011
Crack WPA2 PSK with BackTrack [Using airmon-ng, airodump-ng, aireplay-ng and aircrack-ng]
Introduction:
I have had several people come to me and ask about how to crack WPA2 networks using BackTrack. While cracking WPA2 is actually a fairly simple task, it is also VERY time consuming. Once you have the security key, you have to decrypt it. This is usually done using a bruteforce attack on the encrypted data. Bruteforcing a key could take minutes, hours, days or even weeks. This all just depends on how strong your dictionary is.
In this tutorial, I will guide you through the steps of cracking WPA2 using a bruteforce with John The Ripper.
I will assume that you have already booted Backtrack and have a Konsole window open. I will also assume that you know the name of your wireless interface. For this tutorial, I'll refer to the interface as [INT].
Step 1:
The first thing that you need to do is put your wireless card in monitor mode. This will allow the card to capture all of the data we need. To do this, simply issue airmon-ng start [INT] in your Konsole window.
Step 2:
Now that the wireless crad is monitoring, we need to find a wireless network that uses the WPA2 encryption. To do this, just issue airodump-ng [INT] in the same Konsole window. This will display a list of the wireless networks in range. Choose one that has WPA in the ENC column.
Step 3:
Once you have found your target network (For legal purposes, I'll assume this is your network. ), note the BSSID, the channel, and the ESSID of the network. You'll need this information later on.
I have had several people come to me and ask about how to crack WPA2 networks using BackTrack. While cracking WPA2 is actually a fairly simple task, it is also VERY time consuming. Once you have the security key, you have to decrypt it. This is usually done using a bruteforce attack on the encrypted data. Bruteforcing a key could take minutes, hours, days or even weeks. This all just depends on how strong your dictionary is.
In this tutorial, I will guide you through the steps of cracking WPA2 using a bruteforce with John The Ripper.
I will assume that you have already booted Backtrack and have a Konsole window open. I will also assume that you know the name of your wireless interface. For this tutorial, I'll refer to the interface as [INT].
Step 1:
The first thing that you need to do is put your wireless card in monitor mode. This will allow the card to capture all of the data we need. To do this, simply issue airmon-ng start [INT] in your Konsole window.
Step 2:
Now that the wireless crad is monitoring, we need to find a wireless network that uses the WPA2 encryption. To do this, just issue airodump-ng [INT] in the same Konsole window. This will display a list of the wireless networks in range. Choose one that has WPA in the ENC column.
Step 3:
Once you have found your target network (For legal purposes, I'll assume this is your network. ), note the BSSID, the channel, and the ESSID of the network. You'll need this information later on.
Now you need to stop airodump. This can be done by pressing Ctrl - C combination on the keyboard. After airodump has been stopped, you'll need to start it again, this time writing the packets it collects to a local file. We will need this later for decryption. You can do this by issuing the following command in the same Konsole: airodump-ng [INT]--channel [CH] --bssid [BSSID] -w /tmp/wpa2
Step 4:
In order to collect the security key, we need to capture a 4 - way handshake between a connecting client and the access point. This can be done two ways. You can wait for a new client to connect to the network, or you can deauthenticate an existing client and force it to reassociate. We will force deauthentication. In order for this to work, you will need the MAC address of one of the existing clients on the network. This can be found pretty easily, so I will not cover it in this tutorial. After you have the MAC of a client, issue this command in a new Konsole window: aireplay-ng -0 1 -a [BSSID] -c [CLIENT MAC] [INT]
Finally:
After you have executed the command in step 4, an existing client will be forced to reassociate with the AP and we will be there to collect the 4 way handshake. If this was successful, airodump (in the other Konsole window) will indicate "WPA Handshake:" in the upper right hand corner.
Once airodump has indicated the handshake, we have collected to key and written it to the local file we specified on the end of the command in step 3. The next thing we need to do is decrypt the key. This is an incredibly long, boring task. This is the part that consumes the most time. It could take minutes, hours, days or weeks depending on the speed and performance of your computer. For decryption, we'll use John The Ripper to bruteforce the key. After stopping airodump in the current window, issue the following command:
/pentest/password/jtr/john --stdout --incremental:all | aircrack-ng -b [BSSID -w - /tmp/wpa2*.cap
This command starts John The Ripper. John The Ripper generates all of the possible combination and feeds them in to aircrack, which actually decrypts the key when the right combination is found.
Conclusion:
So, we used John The Ripper, airmon-ng, airodump-ng, aireplay-ng, aircrack-ng and John The Ripper to crack a WPA2 network. As I stated above, the final step can take a VERY LONG time to complete, so allow yourself plenty of time.
If you have any questions or comments, please feel free to let me know!
Did you know that i7's Guide to hacking can be delivered daily to your kindle devices? Subscribe Now!
Friday, July 15, 2011
Decrypt MD5 Hash
Introduction:
The most popular type of encryption for usernames, passwords and other important information is MD5. It is strong, one-way and overall, pretty secure. The only problem is, once you have encrypted so many different strings into an MD5 hash, you begin to realize how the encryption works and begin to realize a mathmatical pattern of sorts.
Due to the everyday use of this encryption, it is now very easy to decrypt an MD5 Hash. The best part is, it doesn't even require any programming.
This post will walk you through the easy step of decrypting a hash using MD5Decryption.com. I will assume you already have your MD5 hash ready and that you have opened MD5Decryption.com in your browser.
Step 1:
Actually, this should be the Finally heading! There is only one major step. Just paste the MD5 string into the text box at the bottom of the page, then choose 'Decrypt'! For this post, we'll use this hash:
The most popular type of encryption for usernames, passwords and other important information is MD5. It is strong, one-way and overall, pretty secure. The only problem is, once you have encrypted so many different strings into an MD5 hash, you begin to realize how the encryption works and begin to realize a mathmatical pattern of sorts.
Due to the everyday use of this encryption, it is now very easy to decrypt an MD5 Hash. The best part is, it doesn't even require any programming.
This post will walk you through the easy step of decrypting a hash using MD5Decryption.com. I will assume you already have your MD5 hash ready and that you have opened MD5Decryption.com in your browser.
Step 1:
Actually, this should be the Finally heading! There is only one major step. Just paste the MD5 string into the text box at the bottom of the page, then choose 'Decrypt'! For this post, we'll use this hash:
5687928ebab58b39f8814dfc33cdfab1
Which decrypts to this string:
testmd5string12
After it checks the hash, it will decrypt it then display it on the screen! Your done!
Labels:
decrypt,
decryption,
hack,
hacking,
md5
Tuesday, July 12, 2011
Create a Live USB Version of BackTrack
Introduction:
There have been several people ask me how to create a Live USB version of the BackTrack Pentesting Suite. This actually happens to be a very easy task, if you know what you are doing. So, I decided to dedicate a post to guide those who aren't quite sure through the process.
Step 1:
You are going to need to make sure you have everything you need, before we start. In order to create the live USB of BackTrack, you're going to need a copy. Visit the BackTrack download page to download the latest copy. With the new version, 5, you have several different options to choose from when downloading. Choose what you want, then either download the ISO directly, or download via a torrent.
The second thing you are going to need is a program called Unetbootin. This program will do the hard work for us. This program, like BackTrack, is also free and can be downloaded from it's Sourceforge page.
Step 2:
Now that you have everything you are going to need, let's begin! The first thing you need to do is launch Unetbootin. This program doesn't come with an installation wizard since it is lightweight. So, if you saved the file in a location somewhere, navigate to it and double click it. If you chose to run the program when downloading, then you should be set! Just make sure it is open.
Step 3:
After Unetbootin loads, shouldn't take but a second, you will need to choose the option for an Disk Image and set the option to ISO. Once you have chosen that, browse for the BackTrack ISO you downloaded earlier. [See image below]
Finally:
Now that you have the basic options set, you need to set the device options. This is VERY important. For the type, choose USB. Then choose the drive letter of your USB Flash Drive that you want to use. Then choose Ok. [See image below]
Unetbootin will now install the files and the bootloader so you can boot BackTrack from your flash drive. This will take a while, just give it time. After it completes, just choose Exit and you're done!
Conclusion:
See, wasn't that easy! Now all you have to do is make sure the drive is plugged in to an available USB port when you boot your computer. Just press the boot key to display the Boot Options, and choose your flash drive!
Did you know that i7's Guide to hacking can be delivered daily to your kindle devices? Subscribe Now!
There have been several people ask me how to create a Live USB version of the BackTrack Pentesting Suite. This actually happens to be a very easy task, if you know what you are doing. So, I decided to dedicate a post to guide those who aren't quite sure through the process.
Step 1:
You are going to need to make sure you have everything you need, before we start. In order to create the live USB of BackTrack, you're going to need a copy. Visit the BackTrack download page to download the latest copy. With the new version, 5, you have several different options to choose from when downloading. Choose what you want, then either download the ISO directly, or download via a torrent.
The second thing you are going to need is a program called Unetbootin. This program will do the hard work for us. This program, like BackTrack, is also free and can be downloaded from it's Sourceforge page.
Step 2:
Now that you have everything you are going to need, let's begin! The first thing you need to do is launch Unetbootin. This program doesn't come with an installation wizard since it is lightweight. So, if you saved the file in a location somewhere, navigate to it and double click it. If you chose to run the program when downloading, then you should be set! Just make sure it is open.
Step 3:
After Unetbootin loads, shouldn't take but a second, you will need to choose the option for an Disk Image and set the option to ISO. Once you have chosen that, browse for the BackTrack ISO you downloaded earlier. [See image below]
Finally:
Now that you have the basic options set, you need to set the device options. This is VERY important. For the type, choose USB. Then choose the drive letter of your USB Flash Drive that you want to use. Then choose Ok. [See image below]
Unetbootin will now install the files and the bootloader so you can boot BackTrack from your flash drive. This will take a while, just give it time. After it completes, just choose Exit and you're done!
Conclusion:
See, wasn't that easy! Now all you have to do is make sure the drive is plugged in to an available USB port when you boot your computer. Just press the boot key to display the Boot Options, and choose your flash drive!
Did you know that i7's Guide to hacking can be delivered daily to your kindle devices? Subscribe Now!
Labels:
backtrack,
hacking,
how-to,
linux,
live,
sourceforge,
unetbootin,
usb
Monday, July 11, 2011
Easily Crack WEP With BackTrack [Using aimon-ng, airodump-ng an aircrack-ng]
Introduction
If you have ever thought about hacking, a wireless network is most likely the first thing you wanted to hack, at least if was for me. While it might seem a little overwhelming, it actually isn't. A WEP network can be hacked in as little as a couple minutes. Yes, WEP is not widely used anymore, but many people still use this encryption for their networks. In this post, I will walk you through the steps of hacking a WEP network and decrypting the key. I will assume that you already have BackTrack booted and have a Konsole window open.
Step 1:
The first thing we need to do is change the MAC Address of the wireless card. We spoof this address so we will be able to associate with the access point. To do this, we first need to put the interface down. We do this by issuing the following command in our open Konsole window: ifconfig wlan0 down
NOTE: Usually, the wireless interface is called wlan0, but in some rare cases, it has been named wlan. To find out which is yours, issue the following command: airmon-ng
Step 2:
Now that the wireless interface has been disabled, we need to spoof our MAC Address. This can be done by issuing the following command in the Konsole window: macchanger --mac 00:11:22:33:44:55 wlan0
Step 3:
Now we need to not only put the wireless interface back up, but we also need to start it in monitor mode. This way we can collect the packets we need to decrypt the key later on. To do this, we simply issue the following command in our Konsole window: airmon-ng wlan0 start
Step 4:
Now we get to start the fun part! We need to find a network the uses the WEP encryption. To see a list of the available networks, run the following command: airodump-ng wlan0
After you have chosen your target network (for legal purposes, I will assume it is yours ), we need to start collecting the packets that are being sent between the access point and the clients. To do this, issue the following command: airodump-ng -c [CHANNEL] -w [FILENAME] --bssid [BSSID] wlan0
NOTE: Replace the brackets ( [] ) and the data inside with the proper values displayed by airdump-ng wlan0.
Step 5:
Now, we have begun collecting packets that are being sent between the access point and the clients. Depending on how many people are using the network, this may take some time. In most cases, there won't be a large number of clients on the network. So, let's speed things up by adding some fake traffic to the network. In order to fake network traffic, the wireless interface has to be associated with the access point. Do this by issuing the following command in a new Konsole window:
If you have ever thought about hacking, a wireless network is most likely the first thing you wanted to hack, at least if was for me. While it might seem a little overwhelming, it actually isn't. A WEP network can be hacked in as little as a couple minutes. Yes, WEP is not widely used anymore, but many people still use this encryption for their networks. In this post, I will walk you through the steps of hacking a WEP network and decrypting the key. I will assume that you already have BackTrack booted and have a Konsole window open.
Step 1:
The first thing we need to do is change the MAC Address of the wireless card. We spoof this address so we will be able to associate with the access point. To do this, we first need to put the interface down. We do this by issuing the following command in our open Konsole window: ifconfig wlan0 down
NOTE: Usually, the wireless interface is called wlan0, but in some rare cases, it has been named wlan. To find out which is yours, issue the following command: airmon-ng
Step 2:
Now that the wireless interface has been disabled, we need to spoof our MAC Address. This can be done by issuing the following command in the Konsole window: macchanger --mac 00:11:22:33:44:55 wlan0
Step 3:
Now we need to not only put the wireless interface back up, but we also need to start it in monitor mode. This way we can collect the packets we need to decrypt the key later on. To do this, we simply issue the following command in our Konsole window: airmon-ng wlan0 start
Step 4:
Now we get to start the fun part! We need to find a network the uses the WEP encryption. To see a list of the available networks, run the following command: airodump-ng wlan0
After you have chosen your target network (for legal purposes, I will assume it is yours ), we need to start collecting the packets that are being sent between the access point and the clients. To do this, issue the following command: airodump-ng -c [CHANNEL] -w [FILENAME] --bssid [BSSID] wlan0
NOTE: Replace the brackets ( [] ) and the data inside with the proper values displayed by airdump-ng wlan0.
Step 5:
Now, we have begun collecting packets that are being sent between the access point and the clients. Depending on how many people are using the network, this may take some time. In most cases, there won't be a large number of clients on the network. So, let's speed things up by adding some fake traffic to the network. In order to fake network traffic, the wireless interface has to be associated with the access point. Do this by issuing the following command in a new Konsole window:
aireplay-ng -1 0 -a [BSSID] -h 00:11:22:33:44:55 wlan0
After you see a message alerting you that association was successful, issue the following command in that same Konsole window:
aireplay-ng -3 -b [BSSID] -h 00:11:22:33:44:55 wlan0
After running that command, your other console window will begin collecting data fairly fast. You can keep an eye on the number of packets collected by the number displayed under the #Data heading in the Konsole running airodump-ng.
Finally:
After you have collected several thousand (You might even need several hundred thousand ) packets, stop everything and run the following command to decrypt the network key:
aircrack-ng -b [BSSID] [FILENAME-01.cap]
This may take a while, just be patient. After aircrack-ng has run, it will let you know whether it was able to decrypt the key or not. If it wasn't, then try it again, only collect more packets. If it was able to decrypt the key, it will display it on the Konsole window!
Conclusion:
Ther you have it! You have just hacked a wireless network using the WEP traffic encryption!
Welcome
Welcome to i7's Guide To hacking. My goal with this blog is to provide step by step guides to hacking into different types of networks and computers. For legal purposes, we'll refer to this as penetration testing on our own networks and computers!
I plan on posting as often as I can, this way those that are eager to learn, can learn as quickly as they like using this blog.
If you have any comments, questions or concerns about anything posted, please feel free to let me know. This is a learning environment... that means you can ask questions and get help without being criticized for it!
I plan on posting as often as I can, this way those that are eager to learn, can learn as quickly as they like using this blog.
If you have any comments, questions or concerns about anything posted, please feel free to let me know. This is a learning environment... that means you can ask questions and get help without being criticized for it!
Subscribe to:
Comments (Atom)